Password management is the practice of securely creating, storing, organizing, and controlling access to passwords and other authentication credentials. It combines human processes with specialized software tools to ensure that every account uses a strong, unique password without requiring users to memorize them all.
Whether you're an individual trying to secure your online life or an IT administrator protecting your organization's digital assets, understanding password management is essential.
This guide explains everything you need to know: what password management is, why it matters, how it works, and how to implement it effectively. You'll learn about different types of password managers, key features to look for, and best practices that protect you from the most common security threats.
Understanding password management
At its core, password management addresses a fundamental challenge: humans are terrible at creating and remembering secure passwords. We default to predictable patterns, recycle familiar combinations across accounts, and prioritize convenience over security.
Password management systems compensate for these inherent limitations by assuming the cognitive burden and complexity on our behalf. As both a practice and a technology, password management encompasses several key functions:
- Password generation: Creating strong, random passwords that meet security requirements and resist common attack methods like brute force and dictionary attacks.
- Secure storage: Encrypting and storing passwords in a protected vault that only authorized users can access.
- Organization: Categorizing and managing credentials across hundreds of accounts, making them easy to find when needed.
- Access control: Determining who can access which passwords, particularly important in team and enterprise environments.
- Autofill and automation: Automatically entering credentials into login forms, reducing friction while maintaining security.
- Audit trails: Recording who accessed which credentials and when, allowing security teams to detect suspicious activity, investigate incidents, and maintain compliance with regulatory requirements.
Password management has evolved from rudimentary practices to sophisticated security infrastructure. The first generation of digital password managers introduced basic encryption (like Blowfish algorithm) and centralized storage, addressing immediate security gaps but lacking the granular controls enterprises required.
Modern password management systems represent a fundamental shift: they combine military-grade encryption, zero-knowledge architecture, role-based access controls, and comprehensive audit capabilities. Today's solutions enforce security policies, detect anomalies, integrate with existing infrastructure, and provide the visibility organizations need to maintain compliance and respond to threats in real time.
Why is password management important?

According to Verizon's 2025 Data Breach Investigations Report, stolen credentials served as the initial access vector in 22% of all confirmed breaches, with that figure jumping to 88% for basic web application attacks.
In the first half of 2025 alone, over 8,000 global data breaches exposed approximately 345 million records, demonstrating the persistent and catastrophic scale of credential-based attacks. Behind these statistics lies a fundamental incompatibility between human cognition and modern security demands.
The human factor
Our brains simply weren't designed for this pace of information. Psychological research shows that humans can reliably remember only 7±2 pieces of data in working memory. Yet we're expected to manage hundreds of unique, complex passwords — each a random string of uppercase letters, lowercase letters, numbers, and symbols.
Faced with this impossible task, people develop coping mechanisms that undermine security:
- Predictable patterns: Adding "123" or "!" to meet complexity requirements.
- Password reuse: Over 60% of people reuse passwords across multiple accounts.
- Writing passwords down: Sticky notes on monitors remain surprisingly common.
- Simple passwords: "password," "123456," and "qwerty" still rank among the most common passwords globally.
This behavior isn't laziness. It's a rational response to an overwhelming cognitive burden. Password fatigue is real, and it leads to security shortcuts.
The consequences of poor password hygiene
When password security fails, the consequences cascade:
- For individuals: Identity theft, financial fraud, privacy violations, and the time-consuming process of recovering compromised accounts. The average victim of identity theft spends 200 hours resolving the issue.
- For businesses: Data breaches cost an average of $4.44 million per incident, according to IBM's Cost of a Data Breach Report. Beyond direct financial losses, organizations face regulatory fines, legal liability, reputational damage, and loss of customer trust.
- For IT teams: Password-related help desk tickets consume 20-50% of IT support resources in typical organizations. Every "forgot password" request represents time that could be spent on strategic initiatives.
The benefits of effective password management
Implementing proper password management delivers measurable improvements:
- Enhanced security: Unique, strong passwords for every account eliminate the domino effect of credential reuse. Even if one password is compromised, your other accounts remain secure.
- Reduced cognitive load: You remember one master password instead of hundreds. The mental relief is immediate and significant.
- Time savings: Autofill eliminates the minutes spent typing or resetting passwords. For organizations, this translates to thousands of hours of productivity annually.
- Compliance support: Many regulations (GDPR, HIPAA, SOC 2) require organizations to demonstrate proper credential management. Password managers provide the audit trails and controls needed for compliance.
- Improved user experience: Seamless access to accounts without the friction of password resets or account lockouts.
How does password management work?
Understanding the mechanics of password management helps you appreciate both its security and its usability. Modern password managers balance strong encryption with user-friendly access.
The master password concept
Everything starts with your master password — the single password you need to remember. This password unlocks your encrypted vault containing all your other credentials.
Many users create master passwords using passphrases, random words strung together like correct-horse-battery-staple, which are both secure and memorable.
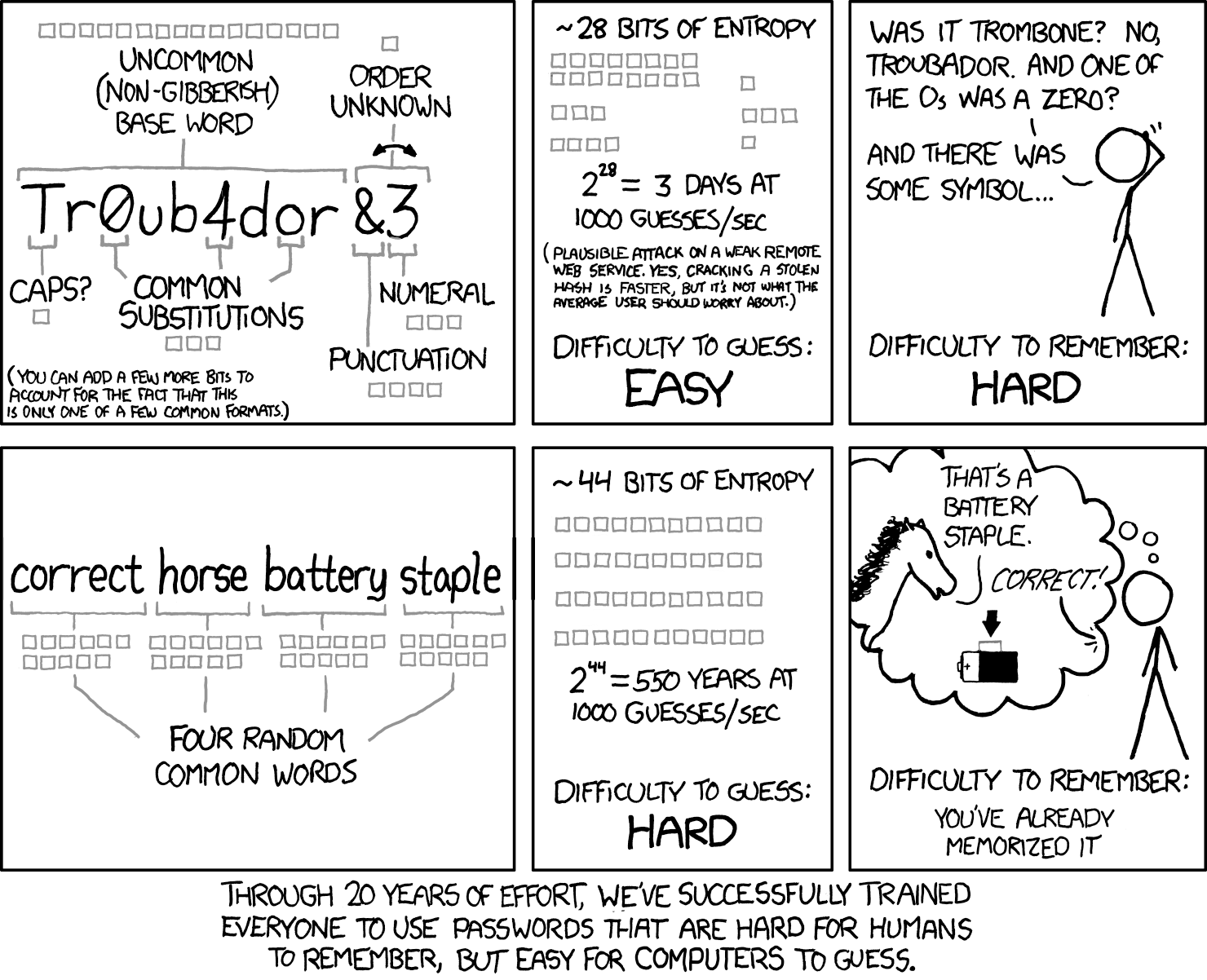
The XKCD comic that popularized this concept demonstrated a crucial insight: four or five random common words create more entropy (randomness) than a shorter complex password, while being far easier to remember.
The encrypted vault
Your password vault is an encrypted database that stores all your credentials, notes, and other sensitive information. Modern password managers use AES-256 encryption, the same standard used by governments and militaries worldwide.
Here's what makes it secure:
- Encryption at rest: Your data is encrypted before it leaves your device. Even the password manager company cannot read your vault contents.
- Zero-knowledge architecture: The service provider never has access to your master password or unencrypted data. If their servers are breached, your passwords remain protected.
- Encryption in transit: When syncing across devices, your encrypted vault travels through secure channels (TLS/SSL), adding another layer of protection.
The user journey
Here's how password management works in practice:
- Initial setup: You create your master password, set up your account and security settings — multi-factor authentication, access controls, and vault parameters.
- Adding passwords: As you log into existing accounts, the password manager detects login forms and offers to save your credentials. You can also manually add passwords or import them from browsers or other password managers.
- Password generation: When creating new accounts, the password manager generates strong, random passwords according to the site's requirements. You never need to think about password creation again.
- Autofill: When you visit a login page, the password manager recognizes the site and offers to fill in your credentials. One click, and you're logged in.
- Syncing: Your encrypted vault syncs across all your devices — phone, tablet, laptop, desktop. Changes made on one device appear everywhere.
- Secure sharing: When you need to share credentials with family members or team members, the password manager encrypts and transmits them securely, without exposing them in plain text.
Types of password managers

Password managers vary significantly in architecture, security model, and deployment options. Understanding these differences is essential for selecting the right solution.
Browser-based password managers
Built into web browsers like Chrome, Firefox, Safari, and Edge, these password managers offer basic functionality without additional software.
Pros:
- Free and immediately available
- Seamless integration with the browser
- Automatic syncing across devices using the same browser
- No learning curve
Cons:
- Limited to browser-only passwords
- Basic security features compared to dedicated solutions
- Vulnerable if browser account is compromised
- Limited sharing capabilities
- Inconsistent cross-browser functionality
Best for: Casual users with simple needs who primarily use one browser ecosystem.
Standalone password managers
These applications store your encrypted password vault locally on your device rather than in the cloud. Designed for individual use, they prioritize local control over multi-device convenience.
Pros:
- Complete control over your data
- No reliance on cloud services
- Works offline
- Maximum privacy
Cons:
- Manual syncing across devices
- Risk of data loss if device fails without backups
- Less convenient for multi-device users
- Requires more technical knowledge
Best for: Privacy-conscious users, those with limited internet connectivity, or anyone who prefers local data storage.
Cloud-based password managers
The most popular category, these services store your encrypted vault on their servers and sync it across all your devices.
Pros:
- Seamless syncing across unlimited devices
- Accessible from anywhere with internet
- Automatic backups
- Rich feature sets (sharing, auditing, breach monitoring)
- User-friendly interfaces
- Mobile apps with biometric authentication
Cons:
- Requires trust in the service provider
- Subscription costs for premium features
- Dependent on internet connectivity
- Potential target for attackers (though encryption protects data)
Best for: Most individual users, families, and small teams who want convenience and comprehensive features.
Enterprise password managers
Designed for organizations, these solutions add administrative controls, compliance features, integration with corporate systems and are deployed on-premise. This architecture eliminates dependencies on external providers. You define the security perimeter, manage access controls, and maintain complete operational independence.
Pros:
- Complete data sovereignty
- Zero external dependencies or cloud service providers
- Automatic compliance with data residency regulations
- Integration with Active Directory, LDAP, and SSO systems
- Centralized administration with granular policy enforcement
- Role-based access controls and privileged access management
- Comprehensive audit logs and compliance reporting
- Automated onboarding/offboarding workflows
- Protection from provider-side security incidents
Cons:
- Higher upfront infrastructure and licensing costs
- More complex setup and administration
- May require IT expertise
- Organization manages backups and disaster recovery
Best for: Businesses of all sizes, IT teams managing shared credentials, organizations with compliance requirements.
Key features of password managers
Modern password managers offer far more than basic password storage. Understanding these features helps you evaluate solutions and maximize their value.
Core features
- Password generation: Creates strong, random passwords based on customizable criteria (length, character types, symbol inclusion). The best generators create passwords that resist brute force attacks for centuries.
- Secure storage: Encrypted vault for passwords, with many managers also storing secure notes, credit card information, identity documents, and other sensitive data.
- Autofill: Automatically detects login forms and fills credentials with one click or tap. Advanced autofill distinguishes between similar sites to prevent phishing attacks.
- Cross-platform syncing: Keeps your vault synchronized across Windows, macOS, Linux, iOS, Android, and web browsers.
- Browser extensions: Integrations for Chrome, Firefox, Safari, Edge, and other browsers that enable autofill and password capture.
- Mobile apps: Full-featured applications for smartphones and tablets, often with biometric authentication.
Security features
- Multi-factor authentication (MFA): Adds a second verification step beyond your master password. Options include authenticator apps (TOTP), SMS codes, hardware keys (YubiKey), or biometric verification.
- Biometric authentication: Unlock your vault using fingerprint, face recognition, or other biometric methods on supported devices.
- Security dashboard: Analyzes your passwords and identifies:
- Weak passwords that don't meet security standards
- Reused passwords across multiple accounts
- Old passwords that haven't been changed recently
- Zero-knowledge architecture: Ensures that even the password manager company cannot access your unencrypted data.
- Emergency access: Designates trusted contacts who can access your vault after a waiting period if you become incapacitated.
Sharing and collaboration features
- Secure sharing: Share individual passwords or entire folders with family members or team members without exposing passwords in plain text.
- Team accounts: Organize passwords by department, project, or access level with role-based permissions.
- Access controls: Define who can view, use, or modify specific passwords.
- Sharing history: Track when passwords were shared, accessed, or modified.
Advanced features
- Password history: Maintains previous versions of passwords, allowing you to revert if needed.
- Secure notes: Store sensitive information beyond passwords — software licenses, WiFi credentials, server details, recovery codes.
- File attachments: Attach encrypted files to vault items (contracts, certificates, documents).
- API access: For developers and power users, programmatic access to the password manager.
- CLI tools: Command-line interfaces for integrating password management into development workflows.
- Audit logs: Detailed records of all vault activities for security monitoring and compliance.
Password management best practices

Having a password manager is only the first step. Following these best practices ensures you're using it effectively and securely.
1. Create an unbreakable master password
Your master password is the single point of failure for your entire password security. Make it count:
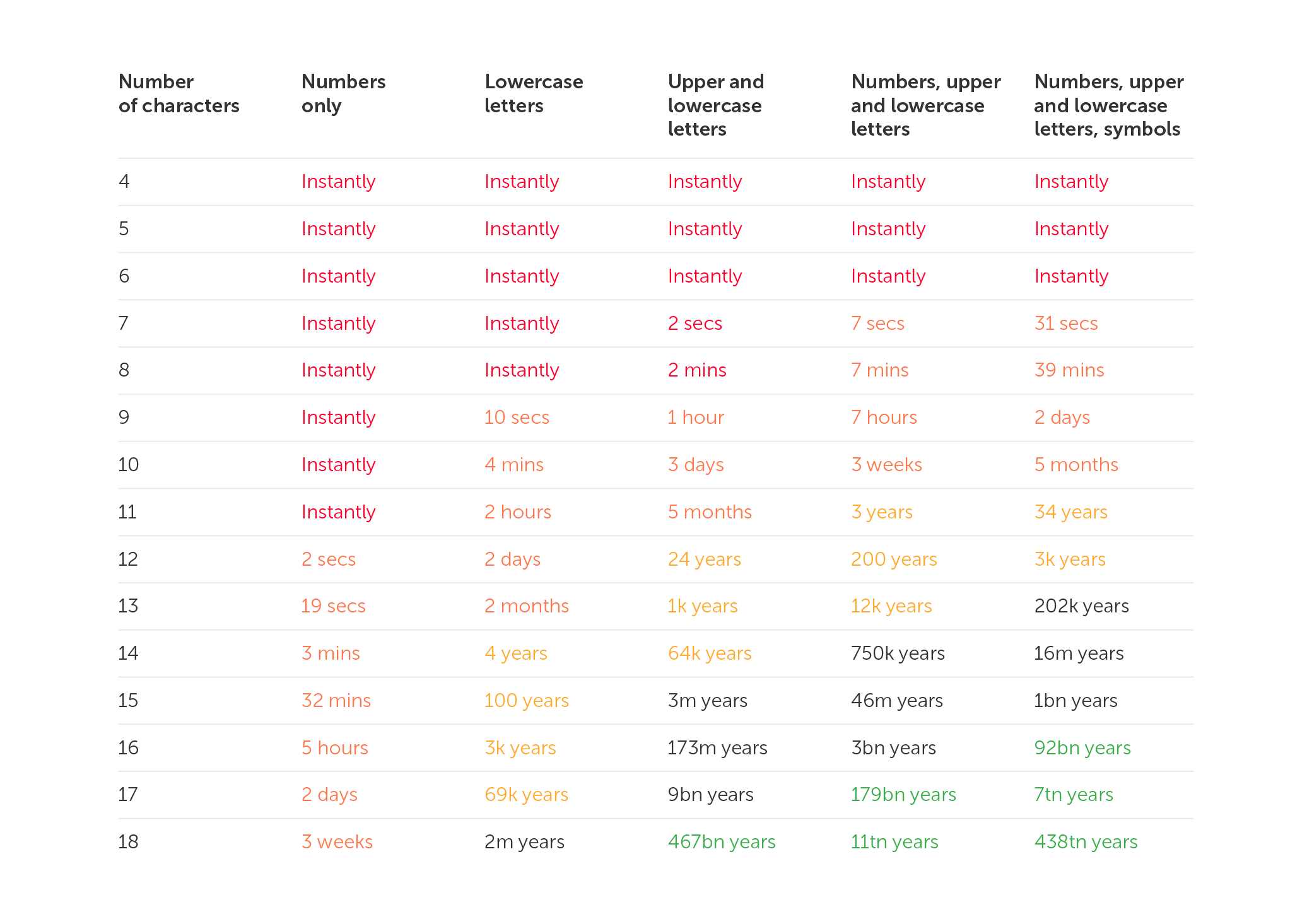
- Use at least 16 characters (longer is better)
- Combine random words into a memorable passphrase
- Avoid personal information (names, dates, addresses)
- Never reuse a password you've used anywhere else
2. Enable multi-factor authentication
Add a second layer of security to your password manager account. Even if someone discovers your master password, they can't access your vault without the second factor. Authenticator apps (Passwork 2FA, Google Authenticator, Authy) are more secure than SMS codes. Hardware security keys (YubiKey) offer the strongest protection.
3. Use unique passwords for every account
This is the fundamental rule of password security. Your password manager makes it effortless — let it generate a unique password for each account. If one site is breached, your other accounts remain secure.
4. Generate long, complex passwords
When creating passwords, maximize length and complexity:
- Aim for 16-20 characters minimum
- Use all character types (uppercase, lowercase, numbers, symbols)
- Let the password manager generate them randomly
5. Conduct regular password audits
Schedule quarterly reviews using your password manager's security dashboard:
- Update weak passwords
- Eliminate reused passwords
- Change old passwords (especially for critical accounts)
- Remove passwords for accounts you no longer use
6. Respond immediately to breach alerts
When your password manager notifies you of a compromised password, change it immediately. Don't wait, breached credentials are often exploited within hours.
7. Organize your vault thoughtfully
Create a logical structure:
- Use folders or tags to categorize passwords (Work, Personal, Finance, etc.)
- Add notes to passwords with security questions, account numbers, or other relevant information
- Mark critical accounts for easy identification
8. Back up your vault regularly
While cloud-based password managers handle backups automatically, consider:
- Exporting an encrypted backup periodically
- Storing the backup in a separate secure location
- Testing your backup to ensure it works
9. Set up emergency access
Designate a trusted person who can access your vault if something happens to you. Most password managers offer emergency access features with configurable waiting periods.
10. Use secure sharing features
When sharing passwords with team members:
- Use the password manager's built-in sharing features
- Never send passwords via email, text, or messaging apps
- Revoke access immediately when no longer needed
- Regularly review who has access to shared passwords
11. Keep your password manager updated
Enable automatic updates to ensure you have the latest security patches and features. This applies to browser extensions, mobile apps, and desktop applications.
12. Avoid common mistakes
- Don't store your master password in your vault (circular dependency)
- Don't share your master password with anyone, ever
- Don't use password manager autofill on public or shared computers
- Don't ignore security warnings from your password manager
- Don't assume you're completely secure — stay vigilant
Frequently Asked Questions

Are password managers safe?
Yes, when properly implemented, password managers are significantly safer than the alternatives (reusing passwords, writing them down, or using weak passwords). They use military-grade AES-256 encryption and zero-knowledge architecture, meaning even the password manager company cannot access your unencrypted data. While no system is 100% invulnerable, password managers have proven track records and are recommended by security experts, including the NSA and CISA.
Can password managers be hacked?
While password managers can theoretically be targeted by attackers, successful attacks are extremely rare and typically require sophisticated techniques. The encryption used is virtually unbreakable with current technology. Most "password manager breaches" you hear about involve compromised user accounts (weak master passwords, no MFA) rather than flaws in the password manager itself. Using a strong master password and enabling multi-factor authentication makes your password manager highly resistant to attacks.
Should I use a free or paid password manager?
Free password managers provide adequate security for basic needs. Paid password managers offer additional features like advanced sharing, priority support, dark web monitoring, and more storage. For individuals, free options are often sufficient. For families and businesses, paid plans provide better collaboration tools and administrative controls. The most important factor is choosing a reputable password manager and using it consistently, regardless of whether it's free or paid.
Can I share passwords safely with family or team members?
Yes, modern password managers include secure sharing features that encrypt passwords before transmission. You can share individual passwords or entire folders with specific people, and you can revoke access at any time. This is far safer than sending passwords via email, text, or messaging apps. Family plans typically allow each person to have their own vault plus shared family folders. Business plans offer more granular permission controls.
Do I need a password manager if I use two-factor authentication?
Yes. Two-factor authentication (2FA) and password managers serve complementary purposes. 2FA adds a second verification step beyond your password, providing protection even if your password is compromised. However, you still need strong, unique passwords for each account — which is what password managers provide. In fact, many password managers can also store and autofill 2FA codes, making the combination even more convenient.
Can I use a password manager on public or shared computers?
It's generally not recommended to use your password manager on public computers (libraries, internet cafes) or shared computers (hotel business centers) due to the risk of keyloggers or other malware. If you must access accounts from a public computer, use your password manager's web vault in a private/incognito browser window, log out completely when finished, and change your master password afterward.
Conclusion
Password management isn't optional anymore — it's essential infrastructure for digital life. The average person manages hundreds of accounts, each requiring secure authentication. Trying to remember unique, strong passwords for every account is impossible, and the alternatives — password reuse, weak passwords, or written notes — create serious security vulnerabilities.
Password managers solve this problem. They generate strong passwords, store them securely with military-grade encryption, and autofill them when needed. You remember one master password; the password manager handles everything else.
The benefits extend beyond security. Password managers save time, reduce frustration, improve productivity, and support compliance requirements. For businesses, they reduce help desk burden and protect against the costly consequences of data breaches.
With on-premise deployment at its core, Passwork ensures complete data ownership, zero-knowledge encryption, and compliance with industry regulations — backed by ISO 27001 certification.
Further reading