Introduction
In the complex ecosystem of modern healthcare, patient data is essential for secure management. In 2024, the U.S. healthcare sector experienced over 700 large-scale data breaches, marking the third consecutive year with such a high volume of incidents. This surge compromised over 275 million patient records, a significant 63.5% increase from 2023.
"Healthcare data are more sensitive than other types of data because any data tampering can lead to faulty treatment, with fatal and irreversible losses to patients" — Healthcare Data Breaches, MDPI
The consequences go far beyond financial penalties and reputational damage. Breaches of electronic Protected Health Information (ePHI) can disrupt patient care, compromise safety, and erode public trust. As the American Hospital Association highlights, since 2020, healthcare breaches have affected over 590 million patient records — more than the entire U.S. population, with a significant number of individuals being affected multiple times.
Healthcare operates in a 24/7 environment where delays in authentication can impact patient care. Systems must provide strong protection without disrupting urgent clinical workflows. Password management is no longer just an IT function. It is now a mission-critical process directly tied to patient safety and regulatory compliance under the Health Insurance Portability and Accountability Act (HIPAA).
How HIPAA works
HIPAA is a U.S. federal law that establishes strict requirements for safeguarding sensitive patient health information from unauthorized disclosure. In addition to privacy protection acts, the HIPAA Security Rule specifically addresses the protection of ePHI, any personally identifiable health information created, stored, transmitted, or received electronically.
HIPAA applies to:
- Covered entities: hospitals, clinics, physicians, insurers, and healthcare clearinghouses
- Business associates: service providers (IT, billing, cloud hosting, consultants) that handle ePHI on behalf of covered entities
HIPAA is structured around several interconnected rules, each serving a distinct purpose in protecting patient data:
- The Privacy Rule sets standards for how PHI can be used and disclosed
- Security Rule defines administrative, physical, and technical safeguards to protect ePHI
- Breach Notification Rule requires covered entities and business associates to notify affected individuals, the U.S. Department of Health and Human Services (HHS), and sometimes the media, in the event of a breach
- The Enforcement Rule outlines penalties for violations
Organizations must document their policies, conduct periodic risk assessments, and ensure that staff are properly trained. Non-compliance can lead to сivil fines up to millions of dollars, criminal penalties, including imprisonment, in cases of willful neglect or malicious misuse, and permanent listing on the public "Wall of Shame" for reported breaches. HIPAA compliance isn’t just about avoiding penalties — it’s about protecting patient safety and trust. A breach of PHI can result in identity theft, financial fraud, and critical interruptions to patient care, underscoring the vital importance of robust healthcare data security.
Cybersecurity and clinical efficiency
The 2024 NIST Digital Identity Guidelines (SP 800-63B) represent a significant evolution in cybersecurity best practices. These guidelines advocate for a shift away from overly complex passwords towards longer, more memorable passphrases, widespread adoption of multi-factor authentication (MFA), and enhanced breach detection capabilities. While these changes undeniably enhance healthcare cybersecurity, they also necessitate that healthcare providers reassess their existing tools and policies to align with modern security paradigms, like Zero trust architecture.
The NIST Digital Identity Guidelines provide a comprehensive framework that complements HIPAA requirements, offering detailed guidance on implementing robust identity and access management. For healthcare organizations, this means:
- Identity proofing. Ensuring that individuals are the ones who they claim to be during the account creation process, reducing the risk of fraudulent access.
- Authenticator Assurance Levels (AALs). NIST defines different levels of assurance for authenticators, from single-factor passwords to strong multi-factor methods. Healthcare organizations should strive for higher AALs for access to sensitive ePHI.
- Federated identity management. Leveraging standards like Single Sign-On (SSO) and LDAP Integration to streamline user access across disparate systems while maintaining strong security controls. This reduces password fatigue and improves overall security posture.
- Lifecycle management. Implementing robust processes for managing identities from creation to deactivation, including timely revocation of access rights for departing personnel. This is crucial for maintaining data integrity and preventing unauthorized access.
By integrating NIST recommendations, healthcare organizations can build a more resilient and adaptable cybersecurity posture in healthcare, moving beyond minimum compliance to proactive risk mitigation. This proactive approach is vital in combating evolving threats such as ransomware attacks and sophisticated phishing campaigns.
HIPAA and password management
The HIPAA Security Rule takes a structured approach to password management, breaking it into administrative and technical safeguards. Together, these safeguards form a framework that organizations must adapt to their operational realities, while still meeting regulatory expectations. All of that is done to keep their patient data secure.
Administrative safeguards focus on policy, governance, and people. They require:
- Documented password policies that define how passwords are created, changed, stored, and removed. These policies must be clear, enforceable, and aligned with risk assessments
- User training programs that educate staff on password hygiene, how to avoid common pitfalls such as reusing or sharing passwords, and how to recognize social engineering attempts. Training must be ongoing, not a one-time event
- Risk-based access controls that ensure staff have only the level of access they need to perform their duties, following the HIPAA minimum necessary principle
- Retention of documentation — all policies, risk assessments, and decisions must be recorded and kept for at least six years, enabling compliance audits and investigations
Technical safeguards address the systems and tools used to enforce secure authentication and access management. They include:
- Authentication mechanisms to verify that the person accessing ePHI is the one who they claim to be — for example, username and password combinations backed up by multi-factor authentication
- Logging and audit trails that record every authentication event and track changes to sensitive data, enabling investigation procedures of anomalies or breaches
- Interoperability, ensuring that authentication and password controls work consistently across all environments — from electronic health record (EHR) systems to medical devices and cloud services
HIPAA further differentiates between required and addressable specifications. Required safeguards are non-negotiable — failure to implement them constitutes non-compliance. Addressable safeguards give organizations some flexibility: they can either adopt the recommended control or implement an alternative that achieves the same level of protection. In either case, the decision must be well-documented, justified, and periodically reviewed to ensure it remains appropriate and effective.
A well-designed password management program under HIPAA doesn’t stop at compliance — it also considers usability, scalability, and the unique pressures of healthcare workflows. Implemented correctly, it can reduce risks without creating operational friction, making secure access part of the daily routine rather than a barrier to patient care.
How to train staff to meet HIPAA standards
Human error remains a primary driver of healthcare data breaches. Therefore, effective staff training is not just a regulatory checkbox but an essential component of HIPAA compliance and overall ePHI protection. While regular, role-specific security awareness training for clinicians, administrators, and IT staff is fundamental, a truly effective program extends far beyond basic awareness. The goal is to transform passive compliance into active participation, empowering employees to be the first line of defense against breaches. Compliance is as much about operational discipline as it is about technology. Healthcare organizations should:
- Implement Role-Based Access Control (RBAC) to enforce least-privilege policies.
- Utilize LDAP Integration and Single Sign-On for centralized onboarding and offboarding processes, enhancing access rights management.
- Separate vaults and permissions by department, specialty, or function to ensure granular control
- Maintain comprehensive audit trails for all credential activities, crucial for accountability and forensic analysis
Organizations should consider incorporating advanced training modules on emerging cybersecurity threats, such as ransomware and advanced persistent threats (APTs), specifically tailored to the healthcare context. This includes practical exercises in incident response, data recovery, and business continuity planning. Furthermore, training should focus on the human element of security and foster a culture of vigilance, making sure that every employee understands their role in protecting sensitive patient data. This can involve gamified learning, interactive workshops, and regular communication channels for security updates and best practices.
How Passwork supports HIPAA compliance
Selecting a password manager for healthcare organizations means not only meeting the highest standards of healthcare data security and regulatory compliance, but also ensuring that the solution fits seamlessly into the daily workflow of medical staff. Complex tools are often rejected in practice, forcing employees to revert to insecure workarounds. Passwork architecture is designed to meet HIPAA-specific compliance challenges while remaining intuitive enough for fast and easy adoption.
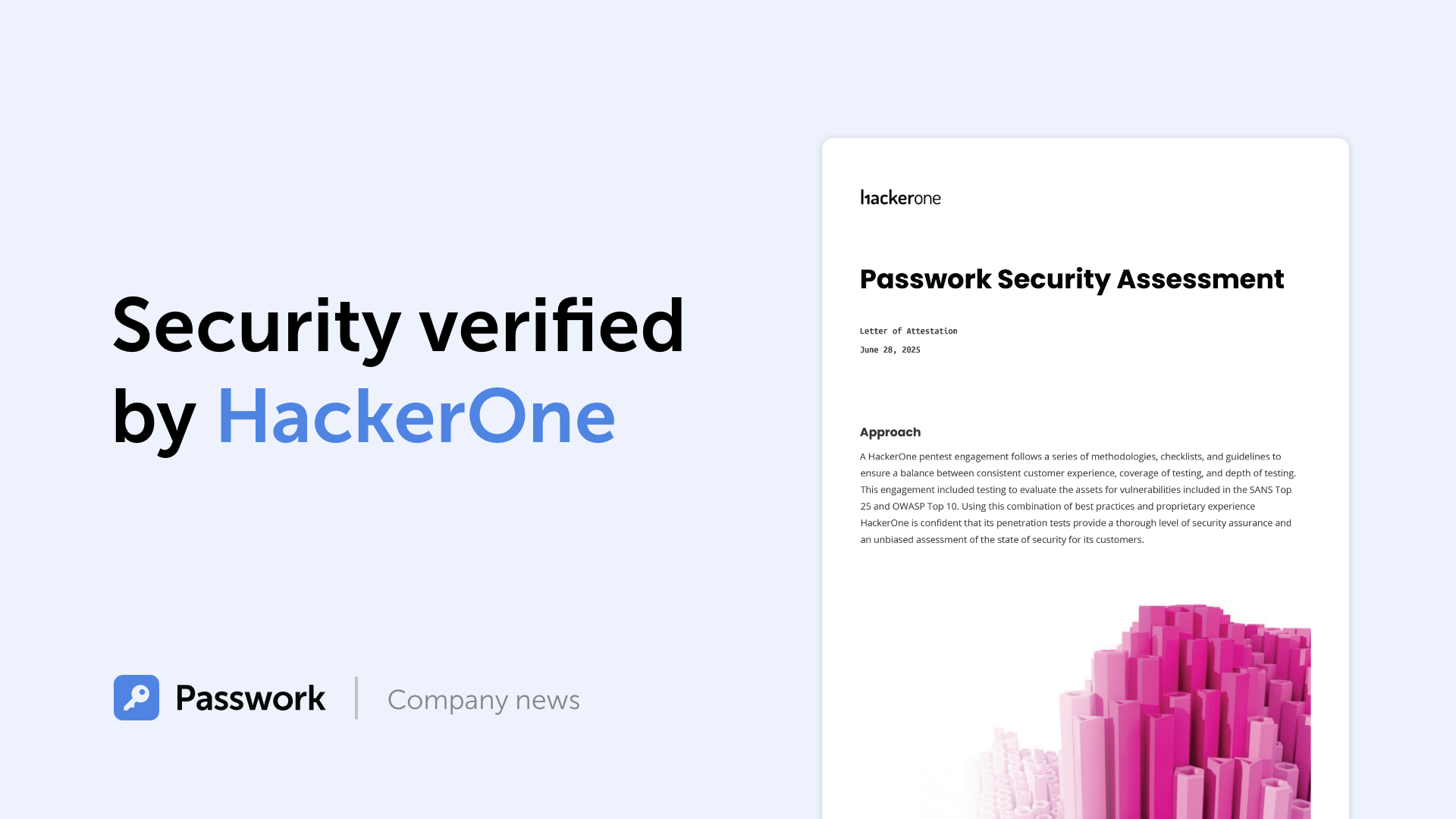
- Certifications and security practices. Passwork is ISO 27001 certified, demonstrating adherence to internationally recognized information security standards. Regular penetration testing via HackerOne ensures the platform remains resilient against emerging threats.
- On-premise deployment. Passwork supports self-hosted deployment, allowing healthcare organizations to run the system entirely within their infrastructure. This approach keeps credentials under direct organizational control, meets HIPAA data protection requirements, and minimizes exposure to third-party risks.
- Data protection by design. With a zero-knowledge architecture and AES-256 end-to-end encryption, Passwork ensures that no one — not even the service provider — can access stored credentials. This aligns directly with HIPAA privacy, security, and technical safeguard provisions.
- Access management. Integration with LDAP and SSO centralizes authentication and user management, making it easier to enforce consistent security policies across large and distributed healthcare environments.
- Granular access control. Passwork RBAC enables administrators to assign precise permissions to each user or group. Only authorized staff can access specific vaults or entries, supporting the HIPAA minimum necessary standard.
- Audit trail and real-time monitoring. HIPAA requires detailed audit controls. Passwork logs all actions, including password creation, modification, sharing, and deletion. Real-time alerts for critical events enable quick detection and response to potential security incidents.
- Multi-factor authentication (MFA). Adding an extra layer of protection, MFA helps safeguard accounts even if a password is compromised.
- Easy onboarding and usability. The clean and intuitive interface allows healthcare staff to start using the system immediately without requiring extensive training or disrupting patient care workflows. Passwork received the "Ease of Use" award from Capterra, which confirms that the solution is user-friendly and does not require extensive training.
By combining advanced security measures, regulatory alignment, and user-friendly design, Passwork enables healthcare organizations to protect ePHI effectively while maintaining HIPAA compliance in a practical, sustainable manner.
Sustainable HIPAA compliance
Achieving compliance is only the first step. Maintaining compliance requires ongoing attention. Healthcare organizations should:
- Conduct regular risk assessments and update policies accordingly
- Review audit logs for anomalies
- Refresh training content annually
- Continuously evaluate tools and workflows against evolving threats and regulatory updates
HIPAA compliance is not just a legal obligation — it is central to fostering patient trust and ensuring patient safety. Secure, efficient password management plays a critical role in protecting ePHI and enabling high-quality care. By combining strong encryption, granular access controls, integration with enterprise systems, and ease of use, Passwork helps healthcare organizations meet and sustain HIPAA compliance. In doing so, it safeguards sensitive data, reduces breach risks, and supports the life-critical mission of healthcare.
Further reading